Token-Based Authentication is a process of authentication and authorization are provided to users by tokens when they access websites or applications. Users use tokens to obtain access to specific resources on a network by encoding their digital signature.
The tokens are always in the form of OTPs (One-Time Passwords), which are randomly generated for each transaction and are intended to be used once.
Authentication based on tokens can be seen as a conversation between two people over the internet. The authentication process is not carried out by two people but rather by code communicating in the background, sharing a secret passcode or agreed-upon symbols to generate a token.
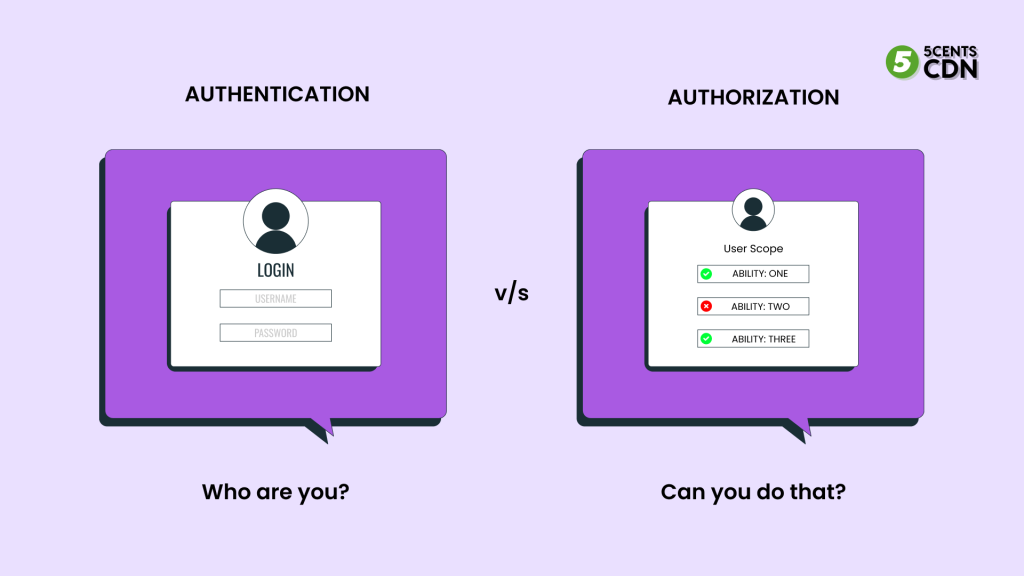
Access to your resources is prevented from unauthorized users by verifying their identity with a token. Also, users don’t have to enter credentials again and again until the token expires, making it easier for them to access the website.
In addition to multi-factor authentication (MFA), tokens can be used to establish communication between applications, APIs and/or websites on the backend.
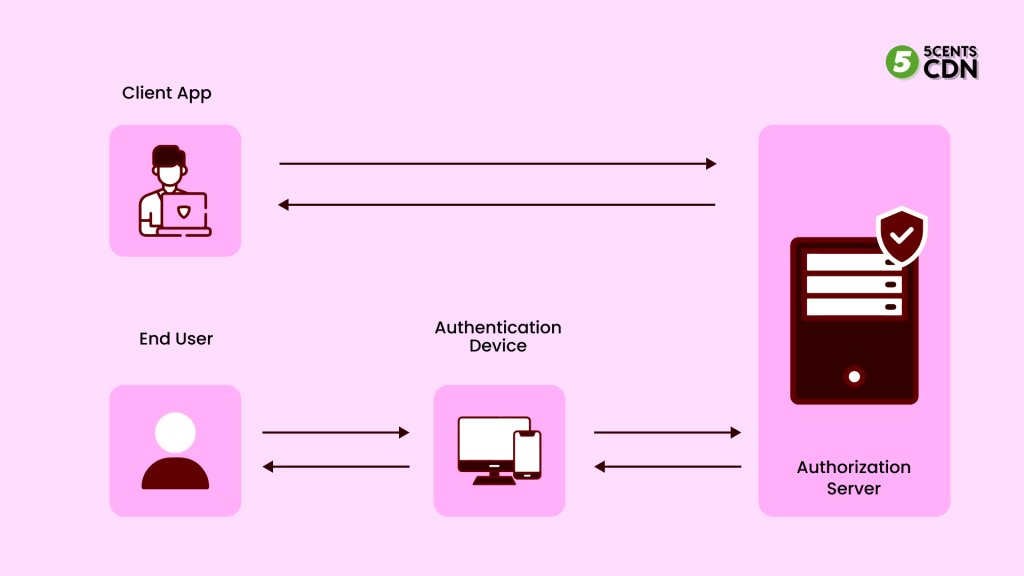
How does a token work?
You must enter your credentials whenever you conduct a transaction online. Your mobile device will receive an OTP via text message or email once you enter your credentials. These random OTPs are generated by a token generator and presented to the website or application for authentication.
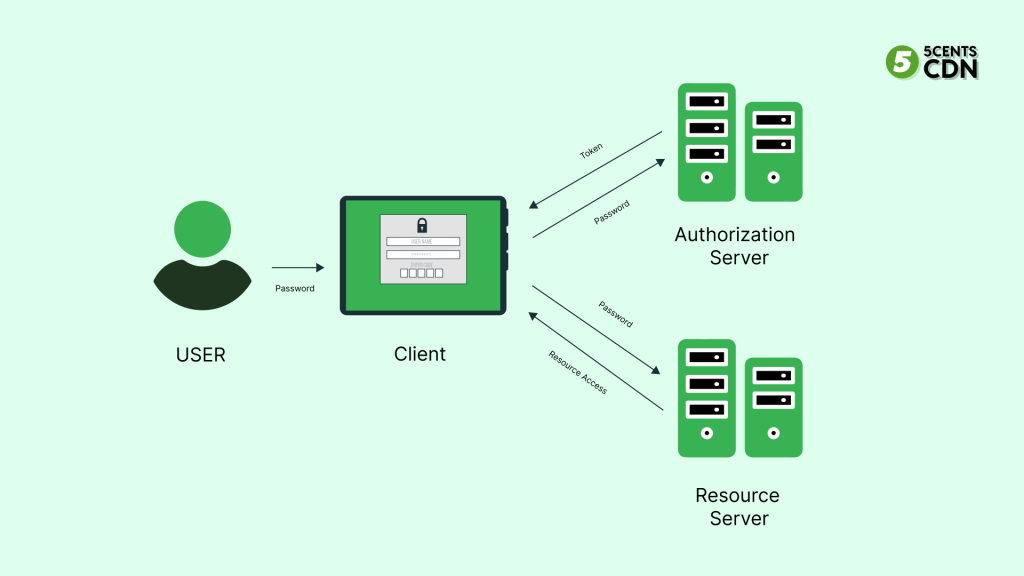
To authenticate the user multiple times during the token lifespan, a random string is sent to the user, which is stored in persistent storage, like web storage. Session tokens are short-lived, and a database table contains all of them, mapped to a user-id, along with information such as expiration dates, device types, and so on.
Importance of token-based authentication
The token is based on a private key that can only be accessed by the device. So external actors cannot interfere with it. Your customers will go with your competitor’s service if you make it too difficult. A token-based authentication solution should strive to verify users without causing friction or frustration. Users will be happy and data will be secure when the authentication process runs smoothly.

Using technology to automate and streamline operations to improve the user experience while reducing staff, poor planning and execution can have a negative impact on the user experience. Take, for example, a bank transaction. Paying bills and ordering checks shouldn’t require separate logins for users checking their bank balances online. Strong authentication can be widely adopted if it is easy to adopt.
Benefits of token-based authentication
There are inherent security advantages to token-based authentication, especially over password-based authentication. Other benefits include
Scalability
Tokens provide a scalable solution since they must be stored at the user’s point of use. A website or application can support many users at once by simply creating and verifying tokens together with the information.
Flexibility
Token-based authentication has the advantage of the flexibility and enhanced performance. It is due to its ability to be used across multiple servers and to provide authentication for various websites and applications at the same time. For a flawless experience, enterprises and platforms can collaborate more easily with each other.
Security
When received at a server-side application that created the token, a secret key can validate it, since JWT tokens are stateless. Thus, they are the safest and most reliable authentication methods.

Token-based authentication Protocols
Using APIs, including RESTful APIs, to communicate with cloud applications is becoming more popular. Our personal information needs to be protected through these connections. In order to implement token-based authentication, there are many tools at our disposal. First, let’s define a few authentication protocols.
Open Authorization – It describes the process by which client-side applications obtain access tokens. There are many types of grants defined by OAuth in order to accommodate different user experiences and flow types.
Security Assertion Markup Language – By providing seamless access to multiple resources with one login credential, you can prevent the proliferation of insecure passwords. As far as identity providers are concerned, SAML does not specify any authentication method
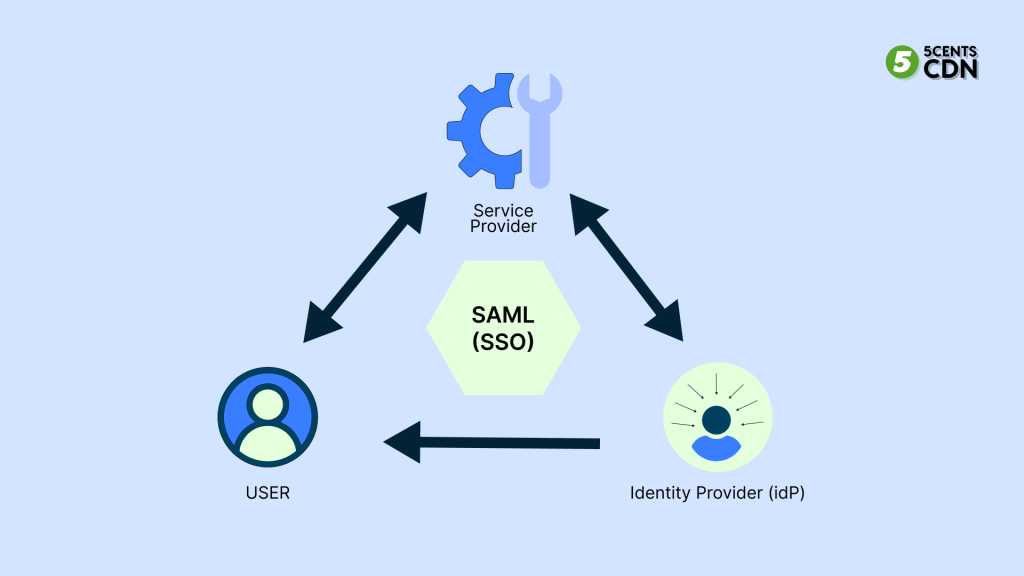
OpenID Connect – OIDC is one of the best ways to connect RESTful APIs to modern web applications. It is becoming more and more important to use OIDC with Single-Page Applications (SPAs).
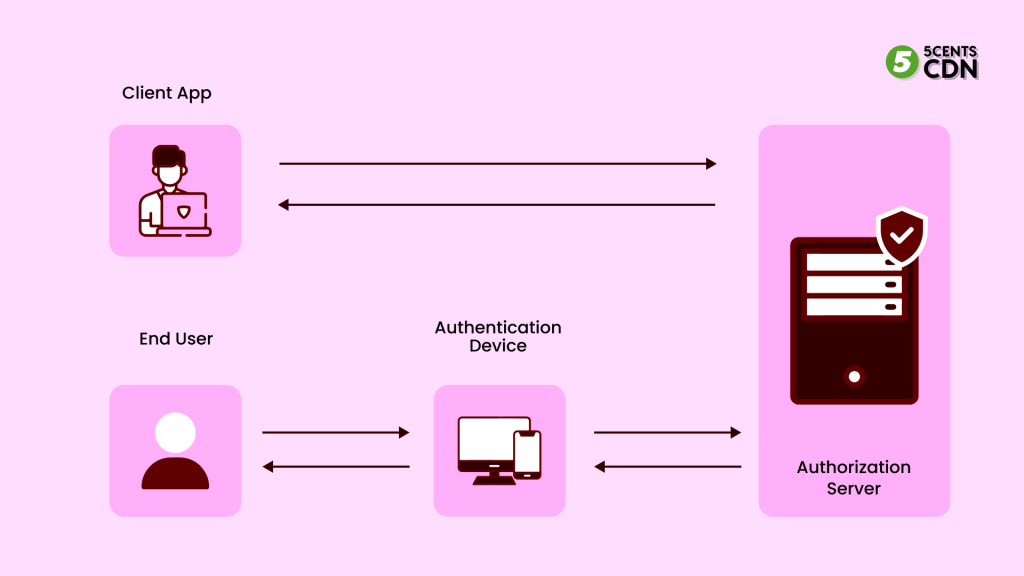
Client Initiated Backchannel Authentication – In essence, it extends the OpenID Connect process. The CIBA application is decoupled from the authentication server, so there are no redirects from the user’s browser to the application.
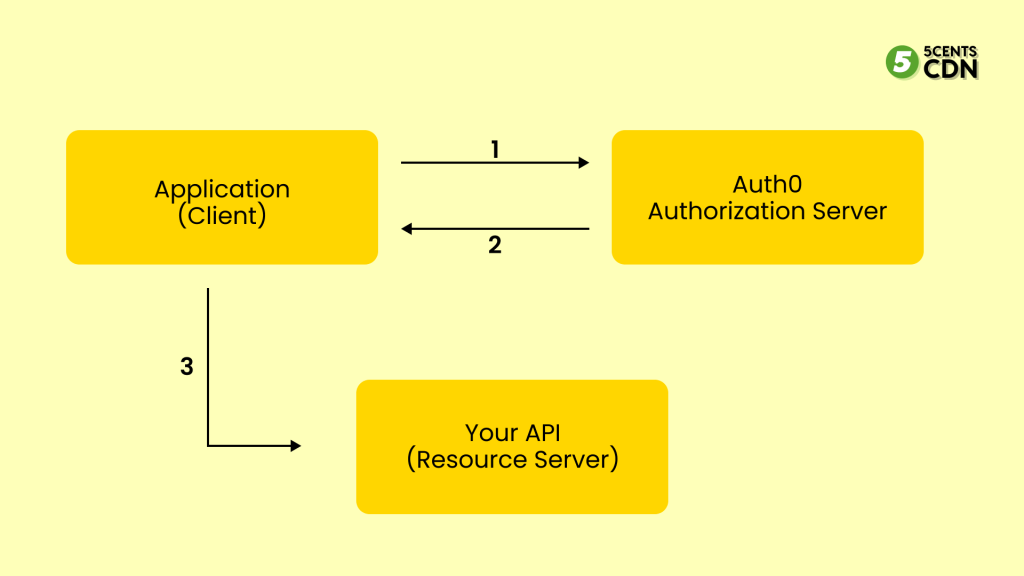
JSON Web Token – There are encoded JSON objects included in this open standard, as well as a set of claims which cannot be altered after a token has been distributed. Users wishing to access APIs, including RESTful APIs, often authenticate themselves using JWT.
Multi-factor authentication (MFA)
As part of multi-factor authentication, hard and soft tokens are typically used after a username and password combination to prove a user’s identity. A hard token is also called a connected token and includes devices you plug into your computers, such as keys and dongles. To authenticate users with authentication servers, one-time passwords or passcodes are generated.
It may be a good idea to incorporate a PIN code as well if you want to make this even more secure. While it might create more friction, by incorporating “something you know” as well as the “something you have” dongle, it engages multi-factor authentication.
On a concluding note, tokens can be leveraged by enterprises based on the nature of their requirements and their individual business needs. It is possible to use JWT in most scenarios if properly implemented and secured by following the correct security measures.