Business across industries is benefiting from rapid digitization by engaging with customers. But bad agents are also taking advantage of this increasing reliance on websites and applications. An organization can be brought to its knees by a well-timed DDoS & other attacks.
A reliable backup plan is key to the best-laid plans. It is largely second nature for cybersecurity professionals to integrate defence networks into a wide variety of technology and data. There have been many benefits and opportunities brought about by the advancement of life online. But it has also been a double-edged sword, as the increased capabilities of websites, applications, and their management interfaces have increased attack surfaces.
Vulnerabilities are more likely to be discovered and exploited by bad actors because of them. A hybrid WAF solution can mitigate the risk associated with DDoS & other attacks. It alone can destroy the entire infrastructure of organizations.
WAF For Defence
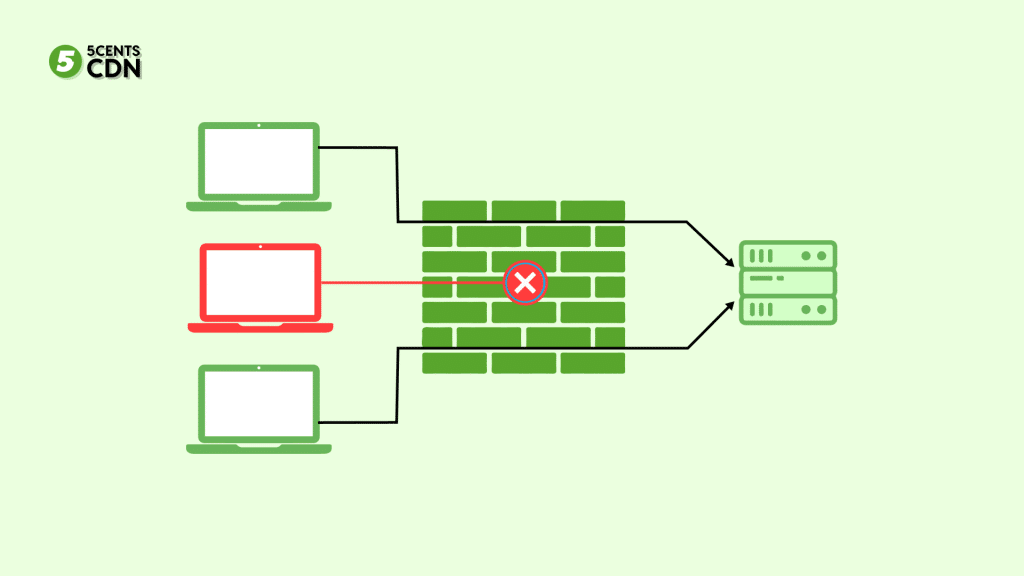
On-premises WAFs are one method of building defence in depth in an organization. It’s helpful if you require close contextual analysis of data right in front of the application server or want to terminate transport-layer security (TLS) within your data centre. Because when combined with an application delivery controller or legacy infrastructure, they can be great for certain needs.
The rules can also be propagated by them and used for internal applications that are not publicly exposed to the internet. Hence they are an excellent choice for applications with no external exposure to the internet.
What do DDoS & other attacks mean?
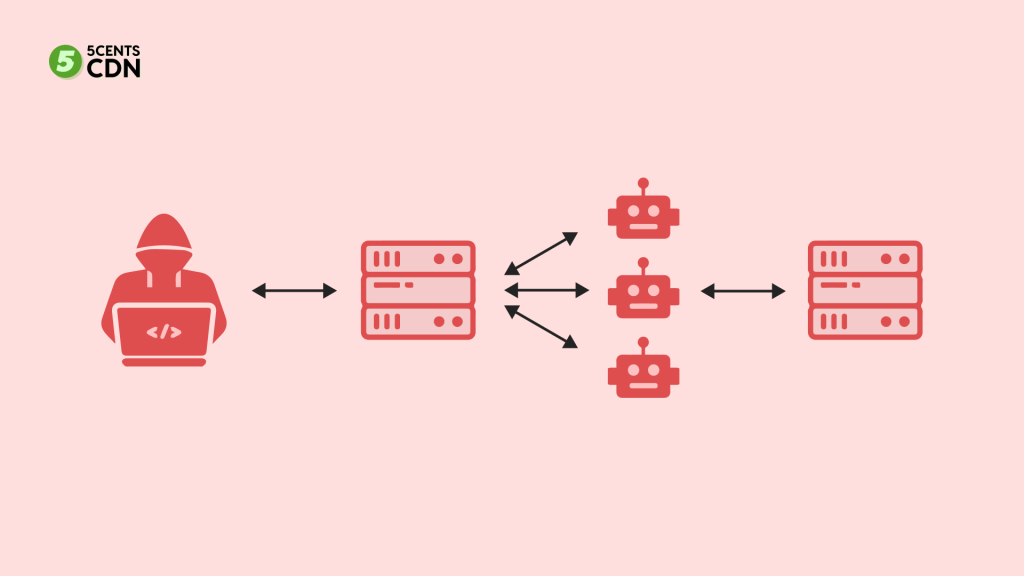
The goal of a DDoS attack is to flood target servers with requests. It basically means sending more than they can handle by using hacked networks. The purpose is to overwhelm a website with fake requests in an attempt to disable it. Attacks like these occur when PCs on different networks with malware flood your website with requests.
3 Types of DDoS & Other Attacks
Companies and industries from a wide range of industries have been targeted by DDoS attacks. Before getting into the prevention details, let’s get to know more about the three different types of these attacks.
- Volume-Based Attacks – An overload of network bandwidth is caused by volumetric DDoS attacks, which send large volumes of traffic to the server such as ICMP and UDP floods.
- Protocol Attacks – Using vulnerabilities in the protocol stack, this type sends malicious requests to Layers 3 and 4, consuming bandwidth from key network infrastructure components. For example, SYN floods and the Ping of Death
- Application Layer Attacks – The application layer i.e. Layer 7 vulnerabilities are exploited in this type of attack. These are the most difficult types of attacks to identify, as they usually involve a small number of requests to accomplish their goal. I.e. low-and-slow attacks and GET/POST floods.
Attacks that don’t crash a website often slow it down. That is enough to make it unusable and frustrating for customers, resulting in reduced revenue. The fact that these attacks are so inexpensive for cybercriminals is likely one reason why they accounted for 35% of all cyberattacks last year. A DDoS attack can be launched on unprotected servers for as little as $100 a day. However, a protected server costs $400 a day.
Protection Against DDoS & Other Attacks
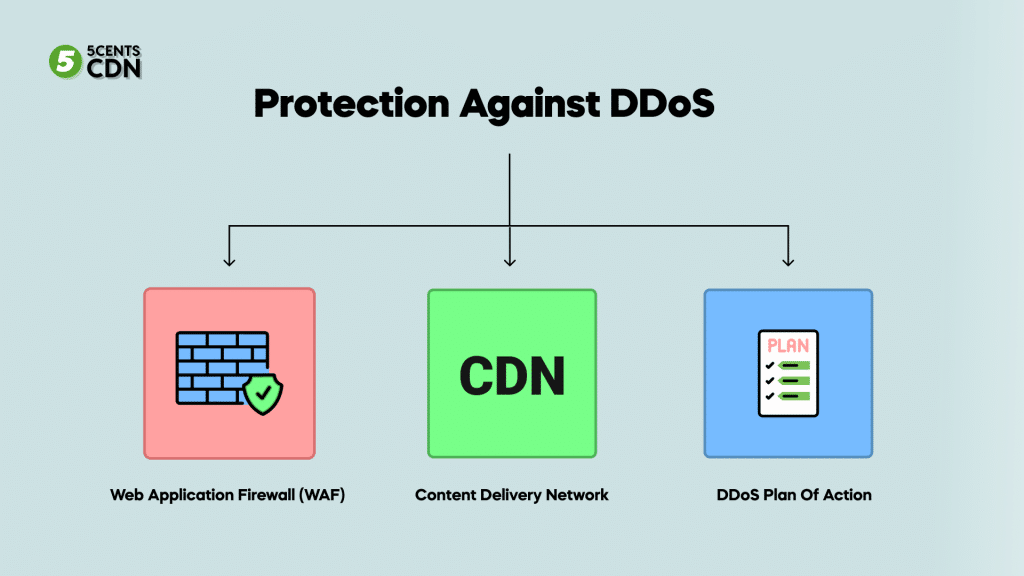
With DDoS protection, you can prevent attacks rather than simply survive them. In recent research, it has been found that approximately 66% of DDoS-targeted sites suffer multiple attacks. Here’s how you can secure your website by avoiding these attacks.
Web Application Firewall (WAF)
In order to distinguish between DDoS attacks and legitimate traffic, web application firewalls (WAFs) are an excellent place to start. An effective WAF will protect your website against these attacks and ensure that your customers are able to access your website without interruption.
Content Delivery Network
The use of a content delivery network (CDN) helps improve website speed and SEO, as well as make your server less vulnerable to attacks by hackers. It’s harder for someone to identify your main server with a CDN since it uses several servers to deliver your content online.
By optimizing via a CDN, you can lower the bandwidth that your primary server has to consume, decreasing the risk of it becoming overloaded. In addition to preventing bad traffic from entering a CDN, its secure port protocol will also help keep it out.
DDoS Plan Of Action
The costs of downtime can range from $137 to $427 per minute for small and midsize businesses, while attacks can cost just $1 per minute. In order to protect the servers, you might want to tell your web hosting provider what’s happening, so they can monitor the traffic and block it.
In contrast, attacking a website for as little as $1 per minute can cost small and midsize businesses between $137 and $427 per minute. A successful attack cannot be outlasted, so the first step is to be aware that you need to act quickly. You may be able to protect your servers by notifying your web hosting service provider, who will monitor and block this traffic. In addition, automate your responses whenever possible, as you’ll need all hands on deck to respond to an attack.
Stay On Top Of DDoS & Other Attacks

In recent years, DDoS threats have evolved rapidly in terms of frequency, duration, maximum Mbps, PPS, and RPS. A company’s website security protocols may become increasingly vulnerable if they don’t update them.
It is no secret that DDoS attacks are on the rise, with a diverse range of industries and companies as targets. The proliferation of larger botnets has also led to a growth in the size and number of these attacks. DDoS attacks have also become more complex due to technological advances. Also, nefarious actors have become more proficient at controlling these larger botnets.
By customizing attacks based on better victim surveillance and varying techniques, durations, and timeframes, they can improve their effectiveness. Therefore, current best practices for mitigating DDoS attacks suggest a hybrid approach to WAF implementation.
On a concluding note, keeping a secure online presence and maintaining a reliable internet presence are undoubtedly high stakes. A prolonged outage of a web-facing asset risks the reputation of the company and is detrimental to its customers. Organizations can mitigate risks and ensure business continuity by engaging security experts and leveraging the available advances.
You can ensure protection against DDoS & other attacks and ways to maximize uptime by getting a reliable CDN for your website.