- Products
- CDN
- Video Service
- Automatic Optimization
- Storage
- Routing and Monitoring
- Edge Delivery
- Delivery Acceleration
- EdgeSec Delivery
- Delivery Acceleration Plus
- Video Delivery
- Live Streaming
- Video Streaming
- Encoding
- Video Encoding
- Live Transcoding
- Stream
- Multistreaming
- Scheduler
- Video Manager
- Player
- Video Player
- Video Player Analytics
- Video Player SDKs (Coming Soon)
- Optimization
- Asset Optimization
- Image Optimization
- Storage
- Cloud Storage
- Critical Backup (Coming Soon)
- Youtube Sync (Coming Soon)
- Realtime User Monitoring
- Web RUM (Coming Soon)
- DNS RUM (Coming Soon)
- Monitoring
- Website (Coming Soon)
- Server (Coming Soon)
- Solutions
- By Industry
- By Need
- IT & Technology
- Image Optimizer
- Website Acceleration
- Asset Optimizer
- WordPress CDN
- E-commerce
- CDN for E-Commerce
- Media & Entertainment
- Video Hosting
- Live Streaming
- IP Camera Streaming
- Live Streaming Events
- OTT Streaming
- Satellite Downlink
- Financial Services
- CDN For Financial Services
- SaaS
- CDN for SaaS
- Web Acceleration
- Wordpress CDN
- Image Optimization
- Asset Optimization
- SaaS Delivery
- Security And Protection
- Bot Protection And Management
- DDoS Protection
- Game Server Security
- Networks
- Pricing
Black Friday Sale Is Live 🎉: Here is your chance to get credits worth up to $400! Discover Our Exclusive Deals Now!
- ProductsCDN
- Edge Delivery
- Delivery Acceleration
- EdgeSec Delivery
- Delivery Acceleration Plus
- Video Delivery
- Live Streaming
- Video Streaming
Video Service- Encoding
- Video Encoding
- Live Transcoding
- Stream
- Multistreaming
- Scheduler
- Video Manager
- Player
- Video Player
- Video Player Analytics
- Video Player SDKs (Coming Soon)
Automatic Optimization- Optimization
- Asset Optimization
- Image Optimization
Storage- Storage
- Cloud Storage
- Critical Backup (Coming Soon)
- Youtube Sync (Coming Soon)
Routing and Monitoring- Realtime User Monitoring
- Web RUM (Coming Soon)
- DNS RUM (Coming Soon)
- Monitoring
- Website (Coming Soon)
- Server (Coming Soon)
- SolutionsBy IndustryIT & TechnologyE-commerceMedia & EntertainmentFinancial ServicesSaaSBy NeedWeb AccelerationVideo StreamingSecurity And ProtectionStorage & Cloud
- Networks
- Pricing
- Log In
- Delivery Acceleration Plus New
- Features
- Talk to an expert
- Try now
- Under attack?




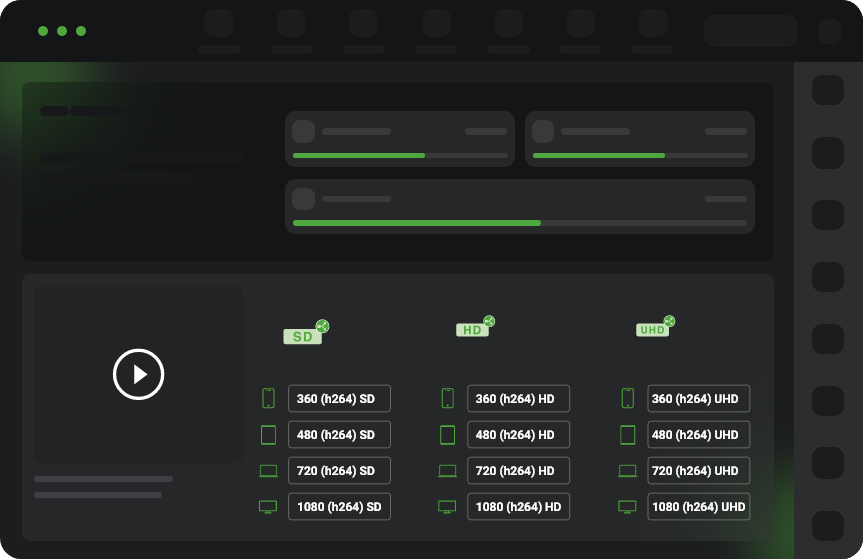

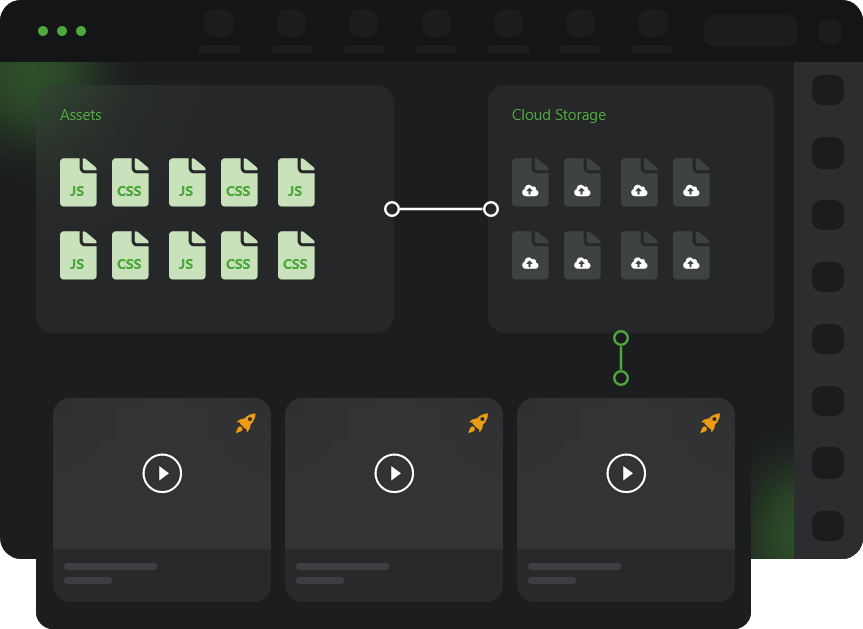
 Traffic Director
Traffic Director